Automotive Experience as basis for Consulting and Training
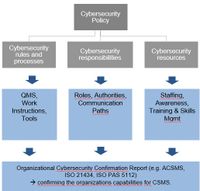
Organizational Cybersecurity Management System
A well-established organisational cybersecurity management system ensures that the following elements are in place, managed and eventually enforced:
- Establish Cybersecurity Governance
- Cybersecurity Culture
- Perform Risk Assessment and Threat Analysis
- Define and Implement Security Requirements
- Vulnerability handling process
- Maintain and Monitor Cybersecurity Over Time
- Ensure Conformity Assessment and Documentation
Establish Cybersecurity Governance
- Define a cybersecurity strategy aligned with the organization's business objectives, consider threats/risks situations, and digital product lifecycle.
- Assign roles and responsibilities e.g. appoint a cybersecurity officer - CISO or designate a responsible team and establish RACI for Cybersecurity tasks
- Establish cybersecurity policies and procedures, covering design, development, supply chain, and vulnerability management. Communicate goals and rules top-down.
We offer our experience in
- Strategy definition
- Evaluation of business objectives
- Required roles and their respective responsibilities
- Conformant cybersecurity policies and procedures
- Thorough communication of goals and rules
- Regular follow-up and management support
Cybersecurity Culture
- Organization should adapt a cybersecurity culture
- Provide regular training to improve the awareness and competency of the resources and maintain the continuous improvement process.
We offer our experience in
- Supporting Workshops in all affected parts of your organization
- Training modules for onsite and online training
Perform Risk Assessment and Threat Analysis
- Identify digital assets and components (hardware, software, interfaces, data).
- Conduct risk assessments regularly across the product lifecycle. Evaluate vulnerabilities and threats (e.g. STRIDE, DREAD).
- Document threat scenarios and potential impacts (e.g. confidentiality, integrity, availability risks).
- Define risk acceptance levels and mitigation concepts
- Define, prioritize, manage and document risk mitigation measures
- Include third-party software and supply chain risks (due diligence required).
Define and Implement Security Requirements
- Integrate security by design and by default into product development
- Implement technical and organizational measures to meet the Essential Requirements:
- Firewalls, network segmentation
- No known exploitable vulnerabilities
- Secure-by-default configuration
- Encryption concepts and mechanisms
- Secure update mechanisms
- Access control (IAM, FMA) and endpoint / data protection
- Limiting attack surface
- Secure data deletion and storage
- Trainings, awareness sessions, security rules and standards for employees
- Incident response plan
- Business Continuity & Recovery Procedures